thick-client testing|thick client penetration testing tools : fabrication During thick client penetration testing, security experts analyze the application for possible security weaknesses. This includes examining the authentication mechanisms, data storage methods, and communication channels. By . 1 de dez. de 2023 · Essa é a minha sincera opinião sobre situações que já estão expostas ao público.Nesse vídeo, comento sobre Raulzito, um youtuber que em 2021 .
{plog:ftitle_list}
WEBDangerous Liaisons 2022 | Maturity Rating: 18+ | 1h 48m | Drama Book smart Célène falls for bad boy Tristan at her new Biarritz high school, unaware she's part of a cruel bet he's made with social media queen .
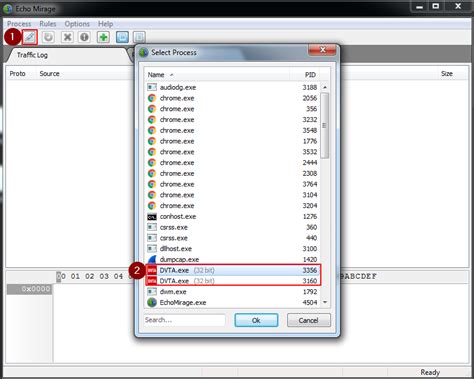
1. Capturing the request via Echo Mirage. Echo Mirage enables intercepting non-HTTP traffic between the tested thick client and the local or remote server. Intercepting requests using this tool, give insight into what kind .This repository serves as a guide for understanding and addressing these challenges, covering various aspects of thick client penetration testing such as information gathering, traffic . What Is Thick Client Penetration Testing? A thick client, also known as a fat client, is a client application that can provide rich functionality, independent of the server in a .During thick client penetration testing, security experts analyze the application for possible security weaknesses. This includes examining the authentication mechanisms, data storage methods, and communication channels. By .
Thick client penetration testing is the systematic evaluation of security measures in desktop applications to discover and address vulnerabilities, enhancing the overall security posture of the software and preventing potential .
In this series of articles, we will learn various tools and techniques used to perform thick client application penetration testing. A step by step breakdown being deployed, we will discuss about starting with the very basics . Thick client penetration testing is an assessment process aimed at evaluating the security of these desktop applications by identifying vulnerabilities, testing authentication mechanisms, assessing data encryption, . Thick Client Penetration Testing [Pentesting] is a feature of Thick Client Security that scans for weaknesses in the Thick Client Application to improve the security of the Application. Thick Client Application Testing .
Thick client penetration testing is a comprehensive security evaluation process to identify and mitigate vulnerabilities in desktops installed on devices. Unlike thin clients, thick clients store .
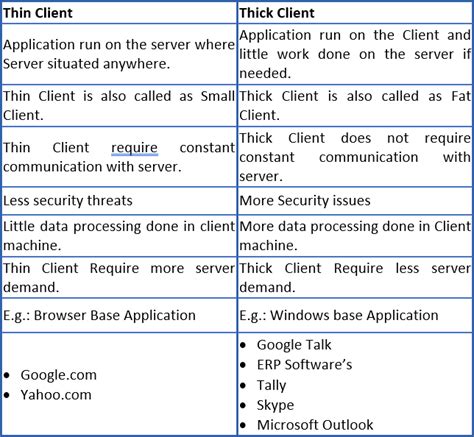
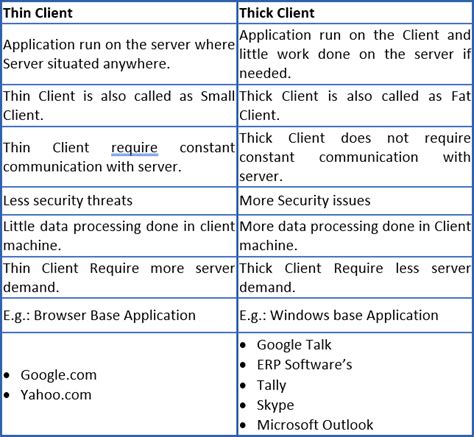
The Hybrid Infrastructure on which the Thick Client Application usually resides poses more security challenges than web-based thin clients. To put it in simple terms, the Thick Client Application runs on the user’s system, .Though, thick client applications are not new, penetration testing process for thick clients is not as straight as Application Penetration testing. It is commonly seen enterprises using thick client applications for their internal operations. Even today, we can find a lot of legacy thick client applications being used by big companies. I have been recently testing many thick client applications. Colleagues and friends have come to me inquiring what my approach is. In this post, I’d like to share my methodology to test thick . Thick clients are also referred to as heavy or fat clients. Thick clients are not dependent on the server’s applications. They have their own operating system and software applications. They have high flexibility and high server capacity. Thick clients have more security threats and are less secure than thin clients. Difference Between Thin .
In the rapidly evolving landscape of cybersecurity, organizations face an increasing challenge to secure their software applications and protect sensitive data. Among the arsenal of defense mechanisms, penetration testing, or "pen testing," has emerged as a vital practice to identify and mitigate vulnerabilities. In this article, we delve into the fascinating world of thick . Thick Client Testing Methodology. Currently, there is no definite methodology when it comes to thick clients because there is no standard. There is an OWASP thick client top 10 but it is still in development. Here is a methodology framework to follow: Information gathering is a critical initial phase in thick client application penetration testing, focused on collecting detailed data about the application’s architecture, components, and interactions with servers. This phase aims to identify communication protocols and potential entry points for exploitation.This course introduces students to the penetration testing concepts associated with Thick Client Applications. This is an entry level to intermediate level course and we encourage you to take this course if you are interested to learn Thick Client Application Security. This course uses a modified version of vulnerable Thick Client Application .
SecureLayer7 begins its thick client application pen testing service by understanding each application's intricacies and functionality. The methodology involves reverse engineering to identify hard-coded secrets, authentication weaknesses, insecure data handling, and potential client-side exploits like buffer overflows and injection attacks .
thick client testing tool
thick client testing methodology
The OWASP Thick Client Project is a standard awareness document for developers and security analyst. It represents the most common security risks identified in thick client applications. . Security Testing Approch. Example. Put whatever you like here: news, screenshots, features, supporters, or remove this file and don’t use tabs at all .
Test for Client-side protection bypass using reverse engineering; Test For Function Exported. Try to find the exported functions; Try to use the exported functions without authentication; Test For Public Methods. Make a wrapper to gain access to public methods without authentication; Test For Decompile And Application Rebuild
The thick client app connects directly to the server, bypassing the application server. This architecture is less secure because the end-user has direct access to the data tier. Types of Thick Client Penetration Testing Methods. Thick client penetration testing involves various methods tailored to different aspects of application security:
Here’s a comprehensive methodology for thick client penetration testing: Thick Client Penetration Testing Methodology 1. Pre-Engagement Preparation.
Thick Client Penetration Testing aims to assess and ensure the secure deployment of thick client or native applications by simulating real-world attacks and analysing potential weaknesses. This comprehensive testing process helps uncover critical vulnerabilities that could be exploited by malicious actors, ensuring that the application’s . Thick client penetration testing is a specialized practice that focuses on identifying and addressing security flaws within these locally executed applications. This blog post aims to delve into . Learn all types of security testing like a black box, white box, and grey-box testing of the thick client application. learn thick client testing with us Thick client (Desktop) application penetration testing is the process of evaluating the security of a thick client application by simulating attacks to identify vulnerabilities. A thick client application, also known as a fat client , is a software program that runs on a local machine and communicates with a server or a database to perform its .
A thick client (or fat client) is a client in client–server relationship. It provides rich functionality, independent of the server, the major processing is done at the client side and can involve only sporadic connections to the server. In this tutorial we demonstrate the process of configuring a .Thick Client Penetration Testing (a.k.a. Thick Client Pentest, Thick Client VAPT, Thick Client Pen Testing) identifies exploitable vulnerabilities on both the local and server-side. The attack surface is larger and requires a different approach from web application penetration testing. Such process often requires specialized tools and custom .
Testing thick client applications for security vulnerabilities requires expert manual penetration testing skills and a thoughtful, methodical approach. NetSPI’s thick client app penetration testing uses multi-vector cybersecurity testing to identify design and configuration weaknesses.Thick client application testing is generally more complicated and customized, involves both local and server-side processing, and often uses proprietary protocols for communication aimed at detecting and identifying loopholes and vulnerabilities before they are exploited for malicious gain. Simple automated scanning is not sufficient and . Introduction to Hacking Thick Clients is a series of blog posts that will outline many of the tools and methodologies used when performing thick client security assessments. In conjunction with these posts, NetSPI has released two vulnerable thick clients: BetaFast, a premier Betamax movie rental service, and Beta Bank, a premier finance .
Proxy-Aware Thick Client: If Thick Client application has a built-in feature to set up a proxy server, then it is known as a proxy-aware Thick Client. Brp Suite (Burp's Invisible Proxy Settings to Test a Non-Proxy-Aware Thick Client Application): Go to Request handling in the Proxy listener window, fill in the appropriate host and port . What are the security testing methods feasible for Thick Client? We can break down the different types of pen testing a thick client into: Dynamic Testing ( fuzzing, traffic interception, injections) System Testing ( checking for logs, data files, registry keys, process threads) Static Testing ( reverse engineering, binary analysis ) Thick client penetration testing is a security assessment process that focuses on identifying and mitigating vulnerabilities in applications that run on client devices, such as desktops or mobile.
Thick client applications can be developed using Java, .Net, C/C++, etc. A thick client may follow two-tier architecture or three-tier architecture. In two-tier architecture, the thick clients directly access the back-end database via the internet. . Thick Client Security Testing - Short Tutorial. by AAT Team Thick Client Penetration Testing . Using frameworks like the CWE Top 25 and OWASP Top 10, we detect vulnerabilities through methods such as buffer overflow and SQL injection while also evaluating cryptography, privilege escalation, and data leakage concerns. Approach. 1. Planning.
thick client pentest checklist
thick client penetration testing tools
Resultado da 5 de dez. de 2023 · O bónus Free Bet de boas-vindas oferecido pela ESC Online 2024 é a oportunidade ideal para começares a ganhar sem .
thick-client testing|thick client penetration testing tools